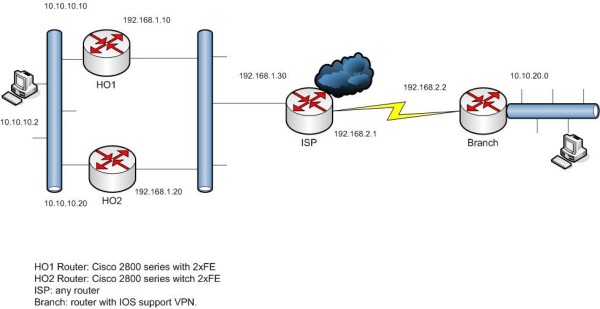
I. Diagram
Gắn cáp theo sơ đồ hình vẽ bên dưới.
Chú ý chọn lựa router có hỗ trợ IPSEC và đủ cổng FastEthernet.
Các switch có thể chia vlan nếu cần thiết (cho các kết nối Ethernet).
Router chi nhánh định kỳ sẽ gửi các thông điệp keepalive đến router HO1. Nếu router Ho1 vì lý do nào đó
Chú ý chọn lựa router có hỗ trợ IPSEC và đủ cổng FastEthernet.
Các switch có thể chia vlan nếu cần thiết (cho các kết nối Ethernet).
Router chi nhánh định kỳ sẽ gửi các thông điệp keepalive đến router HO1. Nếu router Ho1 vì lý do nào đó
II. Cấu hình
Cấu hình của router HO2. Router Ho2 cấu hình VPN với router Branch.
sh run
Building configuration…
Current configuration : 1333 bytes
!
version 12.3
hostname HO2
!
ip cef
!
no ip domain lookup
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 192.168.2.2
no crypto isakmp ccm
!
!
crypto ipsec transform-set myset esp-3des
!
crypto map mymap 1 ipsec-isakmp
set peer 192.168.2.2
set transform-set myset
match address 100
!
interface FastEthernet0/0
ip address 10.10.10.20 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.1.20 255.255.255.0
duplex auto
speed auto
crypto map mymap
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.1.30
!
!
ip http server
no ip http secure-server
!
access-list 100 permit ip 10.10.10.0 0.0.0.255 10.10.20.0 0.0.0.255
!
end
HO2#
Với router Ho1, cấu hình tương tự. ĐốI với router chi nhánh, cấu hình như sau:
!
hostname Branch
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 192.168.1.10
crypto isakmp key cisco address 192.168.1.20
crypto isakmp keepalive 10 3
no crypto isakmp ccm
!
!
crypto ipsec transform-set myset esp-3des
!
crypto map mymap 1 ipsec-isakmp
set peer 192.168.1.10
set peer 192.168.1.20
set transform-set myset
match address 100
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
crypto map mymap
!
interface FastEthernet0/1
ip address 10.10.20.1 255.255.255.0
duplex auto
speed auto
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
!
ip http server
no ip http secure-server
!
access-list 100 permit ip 10.10.20.0 0.0.0.255 10.10.10.0 0.0.0.255
!
end
Branch#
Kết quả debug trên router chi nhánh
Branch#debug crypto isakmp
Crypto ISAKMP debugging is on
Branch#
*Jan 20 13:11:18.095: ISAKMP: received ke message (1/1)
*Jan 20 13:11:18.095: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
*Jan 20 13:11:18.095: ISAKMP: Created a peer struct for 192.168.1.10, peer port 500
*Jan 20 13:11:18.095: ISAKMP: New peer created peer = 0x4668A2A8 peer_handle = 0x80000006
*Jan 20 13:11:18.095: ISAKMP: Locking peer struct 0x4668A2A8, IKE refcount 1 for isakmp_initiator
*Jan 20 13:11:18.095: ISAKMP: local port 500, remote port 500
*Jan 20 13:11:18.099: ISAKMP: set new node 0 to QM_IDLE
*Jan 20 13:11:18.099: insert sa successfully sa = 46F70A18
*Jan 20 13:11:18.099: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
*Jan 20 13:11:18.099: ISAKMP:(0:0:N/A:0):Looking for a matching key for 192.168.1.10 in default
*Jan 20 13:11:18.099: ISAKMP:(0:0:N/A:0): : success
*Jan 20 13:11:18.099: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 192.168.1.10 <- hoàn tất thiết peer với Ho1.
*Jan 20 13:12:08.623: ISAKMP: set new node 231150791 to QM_IDLE
Sau đó router bắt đầu gửi các thông điệp DPD.
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1185424704, message ID = 231150791
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1): seq. no 0x2F4005F4
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1): sending packet to 192.168.1.10 my_port 500 peer_port 500 (I) QM_IDLE
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1):purging node 231150791
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
*Jan 20 13:12:08.623: ISAKMP:(0:5:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1):incrementing error counter on sa: PEERS_ALIVE_TIMER
*Jan 20 13:12:11.623: ISAKMP: set new node 1505333064 to QM_IDLE
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1185424704, message ID = 1505333064
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1): seq. no 0x2F4005F5
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1): sending packet to 192.168.1.10 my_port 500 peer_port 500 (I) QM_IDLE
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1):purging node 1505333064
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
*Jan 20 13:12:11.623: ISAKMP:(0:5:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1):incrementing error counter on sa: PEERS_ALIVE_TIMER
*Jan 20 13:12:14.623: ISAKMP: set new node 1001804729 to QM_IDLE
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1):Sending NOTIFY DPD/R_U_THERE protocol 1
spi 1185424704, message ID = 1001804729
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1): seq. no 0x2F4005F6
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1): sending packet to 192.168.1.10 my_port 500 peer_port 500 (I) QM_IDLE
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1):purging node 1001804729
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_PEERS_ALIVE
*Jan 20 13:12:14.623: ISAKMP:(0:5:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Sau khi tháo cáp trên router HO1 để mô phỏng tình trạng bad, router sẽ báo lỗi sau:
*Jan 20 13:12:17.623: ISAKMP:(0:5:SW:1):incrementing error counter on sa: PEERS_ALIVE_TIMER
*Jan 20 13:12:17.623: ISAKMP:(0:5:SW:1):peer 192.168.1.10 not responding!
*Jan 20 13:12:17.623: ISAKMP:(0:5:SW:1):peer does not do paranoid keepalives.
Sau đó router chi nhánh chuyển sang thiết lập peer với router HO2.
*Jan 20 13:12:19.119: ISAKMP: Created a peer struct for 192.168.1.20, peer port 500
*Jan 20 13:12:19.119: ISAKMP: New peer created peer = 0x4668A2A8 peer_handle = 0x80000007
*Jan 20 13:12:19.119: ISAKMP: Locking peer struct 0x4668A2A8, IKE refcount 1 for isakmp_initiator
*Jan 20 13:12:19.119: ISAKMP: local port 500, remote port 500
*Jan 20 13:12:19.119: ISAKMP: set new node 0 to QM_IDLE
*Jan 20 13:12:19.119: insert sa successfully sa = 46F726A4
*Jan 20 13:12:19.155: ISAKMP:(0:0:N/A:0):Looking for a matching key for 192.168.1.20 in default
*Jan 20 13:12:19.155: ISAKMP:(0:0:N/A:0): : success
*Jan 20 13:12:19.155: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 192.168.1.20
Lúc này, router chi nhánh sẽ thiết lập peer với router HO2 (địa chỉ là 192.168.1.20).
Branch#show crypto isakmp sa
dst src state conn-id slot status
192.168.1.10 192.168.2.2 MM_NO_STATE 5 0 ACTIVE (deleted)
192.168.1.20 192.168.2.2 QM_IDLE 6 0 ACTIVE
Branch#
















Không có nhận xét nào:
Đăng nhận xét